marty45714
Member
4th Update 5/2/2013 - Found a bug... Nothing that would affect the overall functionality, but it could cause some users to think that their phone is successfully connected via USB debugging, when it really isn't.
Update: 5/2/2013 - Per user requests, adding link to VirtualBox download site on the original post.
3rd Update 5/1/2013 - I changed the code that 'finds' the exploit file to make sure it get executed successfully. It's now using the "PATH" environment to do this. This is more reliable than the actual Linux 'find' command I was using before. Also added some additional instructions to clarify some steps based on feedback from users. Finally, added code to detect if the network adapter is not configured correctly. It will alert the user to configure the network adapter properly in the VirtualBox application.
2nd Update 5/1/2013 - I added some lines to the script to stress the importance of pressing one of the three hardware buttons on the phone (Volume up, Volume Down, or Power) once the exploit has been executed. After discussing this with the author of the exploit, this is an important step to obtaining root.
UPDATE 5/1/2013 - New and improved .ova file. Contains improved logic in the exploit script to help with some of the problems that have been encountered by users.
If you've had trouble rooting, please download the new version and try again!
Hey folks, I'm a UNIX admin by profession, so I took the challenge over the weekend to come up with an easy root process for Bionic stock Jelly Bean, specifically for those who aren't familiar with Linux.
I decided to build a Linux VM under Oracle VirtualBox on my Windows PC. This seemed like the logical choice since VirtualBox is free, a relatively small download, is easy to install and it's easy to import VMs.
My first attempt was using CentOS Linux. It worked, but the file required for users to download was over 450MB... Back to the drawing board!
Started looking for very small Linux distros and found Tiny Core Linux. This worked well. The file required for download is 46MB.
Everything you need to root the Bionic is here and it is automatic. The process will walk you through connecting to the Samba file share, connecting the phone in USB debugging mode, and OF COURSE, it will run the process to root the phone.
Here are the steps:
1) Install Sun VirtualBox on your Windows PC.
http://download.virtualbox.org/virtualbox/4.2.12/VirtualBox-4.2.12-84980-Win.exe
Note: We've had one report that this file also works with VMWare Workstation and VMWare Player. If you don't want to install VirtualBox feel free try the file with VMWare.
2) Download the VirtualBox .ova file containing the Linux VM from one of the following links:
http://www.knite.net/Bionic/Root_Bionic_JB_20130501-4.ova
Root_Bionic_JB_20130501-4.ova
https://dl.dropboxusercontent.com/s...fhiAIiSwc0jD1AdVFNY27QdoeKP9ot_7IdDetSvw&dl=1
3) Import the .ova file into VirtualBox. (Click "File" then "Import Appliance".)
4) Start the imported VM in VirtualBox (Click the big "Start" Button. It has a green arrow icon.)
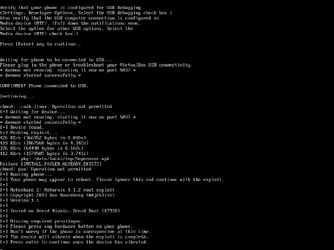
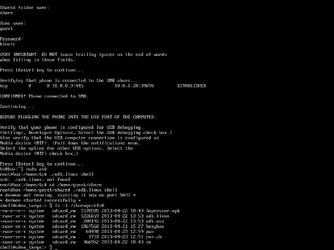
5) Follow the instructions on the Linux console.
That should do it. If you need help I will be monitoring this thread.
Update: 5/2/2013 - Per user requests, adding link to VirtualBox download site on the original post.
3rd Update 5/1/2013 - I changed the code that 'finds' the exploit file to make sure it get executed successfully. It's now using the "PATH" environment to do this. This is more reliable than the actual Linux 'find' command I was using before. Also added some additional instructions to clarify some steps based on feedback from users. Finally, added code to detect if the network adapter is not configured correctly. It will alert the user to configure the network adapter properly in the VirtualBox application.
2nd Update 5/1/2013 - I added some lines to the script to stress the importance of pressing one of the three hardware buttons on the phone (Volume up, Volume Down, or Power) once the exploit has been executed. After discussing this with the author of the exploit, this is an important step to obtaining root.
UPDATE 5/1/2013 - New and improved .ova file. Contains improved logic in the exploit script to help with some of the problems that have been encountered by users.
If you've had trouble rooting, please download the new version and try again!
Hey folks, I'm a UNIX admin by profession, so I took the challenge over the weekend to come up with an easy root process for Bionic stock Jelly Bean, specifically for those who aren't familiar with Linux.
I decided to build a Linux VM under Oracle VirtualBox on my Windows PC. This seemed like the logical choice since VirtualBox is free, a relatively small download, is easy to install and it's easy to import VMs.
My first attempt was using CentOS Linux. It worked, but the file required for users to download was over 450MB... Back to the drawing board!
Started looking for very small Linux distros and found Tiny Core Linux. This worked well. The file required for download is 46MB.
Everything you need to root the Bionic is here and it is automatic. The process will walk you through connecting to the Samba file share, connecting the phone in USB debugging mode, and OF COURSE, it will run the process to root the phone.
Here are the steps:
1) Install Sun VirtualBox on your Windows PC.
http://download.virtualbox.org/virtualbox/4.2.12/VirtualBox-4.2.12-84980-Win.exe
Note: We've had one report that this file also works with VMWare Workstation and VMWare Player. If you don't want to install VirtualBox feel free try the file with VMWare.
2) Download the VirtualBox .ova file containing the Linux VM from one of the following links:
http://www.knite.net/Bionic/Root_Bionic_JB_20130501-4.ova
Root_Bionic_JB_20130501-4.ova
https://dl.dropboxusercontent.com/s...fhiAIiSwc0jD1AdVFNY27QdoeKP9ot_7IdDetSvw&dl=1
3) Import the .ova file into VirtualBox. (Click "File" then "Import Appliance".)
4) Start the imported VM in VirtualBox (Click the big "Start" Button. It has a green arrow icon.)
5) Follow the instructions on the Linux console.
That should do it. If you need help I will be monitoring this thread.