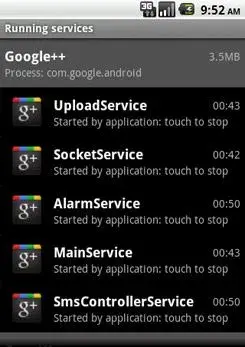
It’s that time again. Time for another string of Android malware, this time using the popularity of Google+ to fool unsuspecting Android users. The malicious code dubbed “Nickispy.C” was discovered by Trend Micro today and although it uses many of the same services as its previous versions, it learned a few new tricks this time around. Now, Nickispy.C goes incognito my calling itself Google++ using the same icon as the legit Google+ app for all of its services.
If given free reign over your phone, the app steals the usual text messages, GPS positions, call logs, and even goes as far as answering your calls allowing for the malware’s creator to listen in or record your most intimate conversations. Still unknown is if this malware made it into users’ devices through the Android Market or 3rd party app store or via the word wide web.
The good news? Well, the malware only effects Android 2.2 users thanks to the exploit being patched up in 2.3 that allows for an app to change the phone state without a user’s consent. The bad news? Android 2.2 is still found on around 74% of all Android devices. Damn. Even more reason to look forward to Android 2.3, right?
SOURCE: New Android malware fakes Google+ to spy on phone calls | Electronista